Someone is Creampie | Adult Movies Onlinecreeping around the digital infrastructure of United States power plants, including a nuclear facility.
Hackers have been breaking into the administrative computer networks of U.S. plant operators since May, using tactics associated with a well-known Russian group, according to The New York Times.
SEE ALSO: Alleged hackers behind NotPetya cyberattack demand $260,000 bitcoin ransomThose tactics include phishing attempts like designing resumes of engineers that have dangerous code embedded in the documents, as well as infecting sites commonly accessed by employees of the place they're trying to compromise.
According to Bloomberg, Russia is a "chief suspect" in the hacking attempts.
The hacks themselves have had mixed results. While the hackers have succeeded in some ways — accessing computers of employees who work at power and nuclear facilities — they have so far failed in a larger sense, as they've been unable to access operating systems of the plants themselves. Computer networks that employees use to send emails and other tasks are not usually the same networks on which plants run.
“There was absolutely no operational impact to Wolf Creek (the nuclear plant breached in the hacks). The reason that is true is because the operational computer systems are completely separate from the corporate network,” Jenny Hageman, a spokesperson from the Wolf Creek, told Bloomberg News.
Still, despite being unable to break into U.S. plants' operating systems, the general concern about plant hacking isn't negligible. If the Russian government is indeed coordinating the hacking attempts, it could signal potential successful hacks in the future, on a much larger scale. Russian hackers have already caused havoc in the Ukrainian electrical grid at least twice since 2015. With the recent hacking attempts against the U.S., Russian hackers might be poking around for ways to access a backdoor in the operating system of certain power plants so they can barge in and take control when they feel the time is right.
Nuclear plants have backup generators that make them difficult to simply knock out, according to Bloomberg, but the U.S. should be the first nation to understand that this doesn't mean a cyber weapon can have no physical impact on the integrity of a nuclear facility.
Nearly a decade ago, the U.S. and Israeli governments built a cyberweapon called Stuxnet that wrecked Iranian nuclear centrifuges and threw Iran's nuclear enrichment program into disarray.
These new hacking attempts targeting U.S. power plans are far less sophisticated than Stuxnet. What's happened since May isn't a "cyberattack" so much as it is a hack.
But if the hacks turn into attacks, it's not like there wasn't any evidence foreshadowing what was to come.
Topics Cybersecurity
(Editor: {typename type="name"/})
 Dyson V8 Plus cordless vacuum: $120 off at Amazon
Dyson V8 Plus cordless vacuum: $120 off at Amazon
 The best memes of 2022
The best memes of 2022
 What is TikTok's watermelon 'Filter for Good'?
What is TikTok's watermelon 'Filter for Good'?
 UK's Bank of England reveals new King Charles III notes
UK's Bank of England reveals new King Charles III notes
 Best Hydro Flask deal: Save $10 on a 24
Best Hydro Flask deal: Save $10 on a 24
Best robot vacuum deal: Save $140 on roborock Q7 Max Robot Vacuum
 SAVE $140:As of May 14, the roborock Q7 Max Robot Vacuum and Mop is on sale for $159.99 at Amazon. T
...[Details]
SAVE $140:As of May 14, the roborock Q7 Max Robot Vacuum and Mop is on sale for $159.99 at Amazon. T
...[Details]
'Vagina on a chip' to aid drug research
 Scientists at the Wyss Institute at Harvard University have created a "vagina on a chip" to further
...[Details]
Scientists at the Wyss Institute at Harvard University have created a "vagina on a chip" to further
...[Details]
STIs are rife over the holidays. Here’s how to keep yourself safe.
 Let’s face it, sexually transmitted infections (or STIs) are probably not the first thing to c
...[Details]
Let’s face it, sexually transmitted infections (or STIs) are probably not the first thing to c
...[Details]
Purfect Prose: An Appreciation of Kitty Litterature
 Purfect Prose: An Appreciation of Kitty LitteratureBy Jeffery GleavesAugust 8, 2017From the ArchiveF
...[Details]
Purfect Prose: An Appreciation of Kitty LitteratureBy Jeffery GleavesAugust 8, 2017From the ArchiveF
...[Details]
The Story Behind the Home of Forgotten Video Games
Meet the graphic designer behind New York Magazine's viral nepotism baby map
 This week, New York Magazine declared 2022 "The Year of the Nepo Baby" and published a thorough visu
...[Details]
This week, New York Magazine declared 2022 "The Year of the Nepo Baby" and published a thorough visu
...[Details]
Elon Musk's Twitter CEO resignation poll gets a cheeky response from MySpace Tom
 Despite the fact Elon Musk's Twitter polls clearly aren't going all that well, the social media plat
...[Details]
Despite the fact Elon Musk's Twitter polls clearly aren't going all that well, the social media plat
...[Details]
 Sam Shepard, 1943–2017By The Paris ReviewJuly 31, 2017In MemoriamSam Shepard, 1983. Photo: Steve Rin
...[Details]
Sam Shepard, 1943–2017By The Paris ReviewJuly 31, 2017In MemoriamSam Shepard, 1983. Photo: Steve Rin
...[Details]
NYT mini crossword answers for May 12, 2025
 The Mini is a bite-sized version of The New York Times' revered daily crossword. While the crossword
...[Details]
The Mini is a bite-sized version of The New York Times' revered daily crossword. While the crossword
...[Details]
Little Red and Big Bad, Part 4
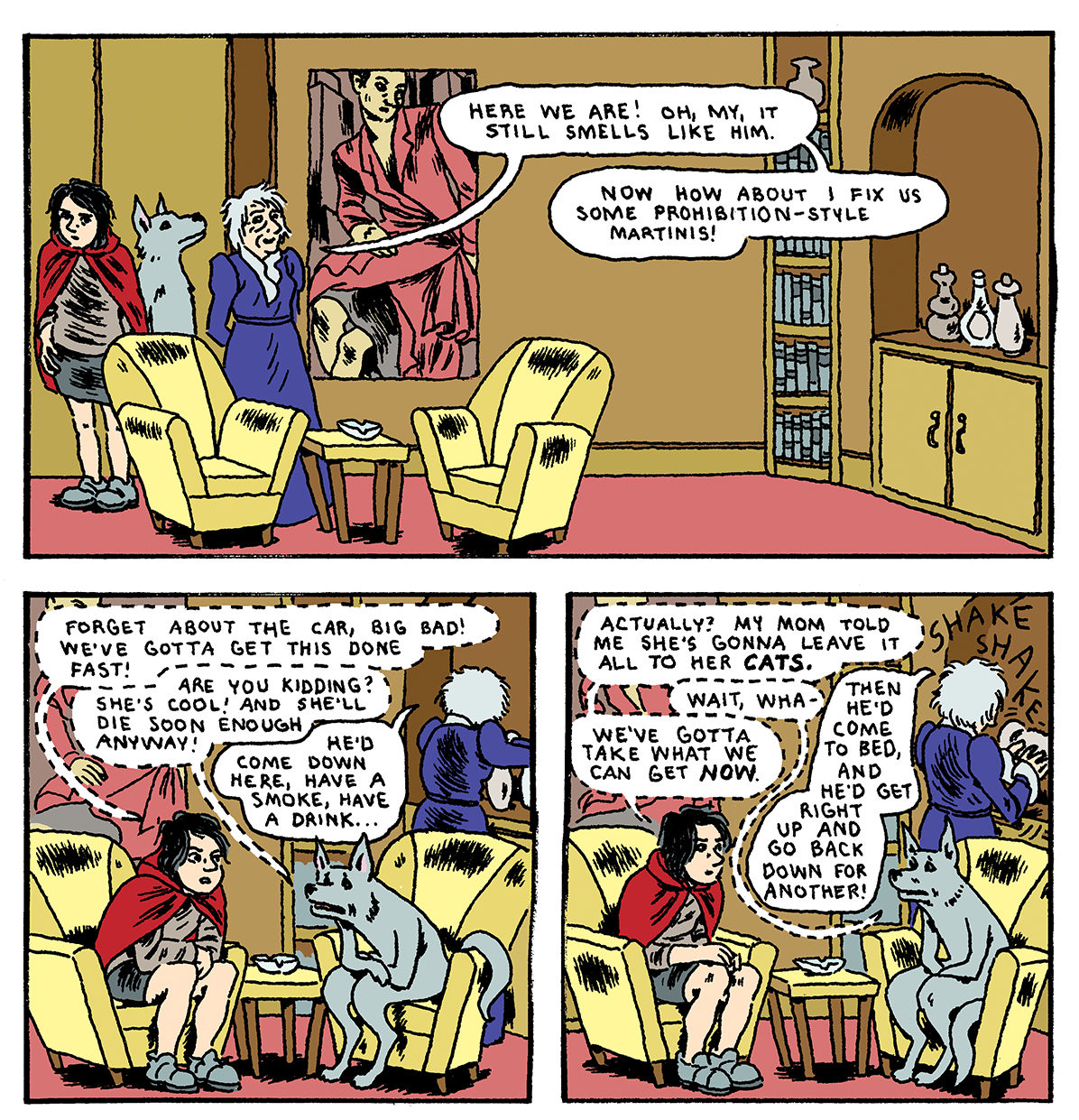 Little Red and Big Bad, Part 4By Gabrielle BellAugust 28, 2017Our CorrespondentsRead earlier install
...[Details]
Little Red and Big Bad, Part 4By Gabrielle BellAugust 28, 2017Our CorrespondentsRead earlier install
...[Details]
接受PR>=1、BR>=1,流量相当,内容相关类链接。